Spammers always use creative ways to grab user attention. Today I noticed the following post in my Facebook news feed.
WhatsApp is a popular messenger app on mobiles and this post promises the same WhatsApp for PCs as well. That should be enough to attract the attention and clicks of a huge number of users.
Clicking on this link could actually give you WhatsApp on your PC, or it could be a spam link that tricks you in to giving away your facebook account details or even worse it could try and install malware on your system.
To find out which of these three actually happens we need to investigate the link in that post without actually clicking on it.
The link in the post is http://bit.ly/whatsappatsolutionbuzz , let's start our analysis by visiting this page through IronWASP. We go to the 'Manual Testing' section of IronWASP and click on the 'Create New Request' button, this lets use create a new HTTP Request equivalent to visiting this link from the browser.
The 'New Request Creation' wizard opens up, we enter the URL in this wizard and hit next.
And then we give this request a name to easily remember and track it. Since this is the first link we are visiting, let's name it as 'FirstLink' and then click on 'Create Request'.
Now we can see the created request. Let's send this by clicking on the 'Send Request' button. This is more or less technically equivalent to visiting the same URL in your browser but without the risk of being infected.
The response from the server is a 301 redirect and the location to which we are being redirected is http://new.solutionbuzz.com/test.php
solutionbuzz.com is not a domain name that I have heard of and I am not sure if this site is safe or if it serves malware. So let's visit this URL also using IronWASP but this time let's add a twist to it. If this site is serving malware then it would have mechanisms to detect if you are sending a request from a browser and if so what browser you are using. This can be determined by checking the User-Agent header in the request. In addition to the user-agent header a browser typically sends a bunch other headers with each request. The first request we created did not have any of these headers and so it would be easy to determine that the request was not actually sent from a browser.
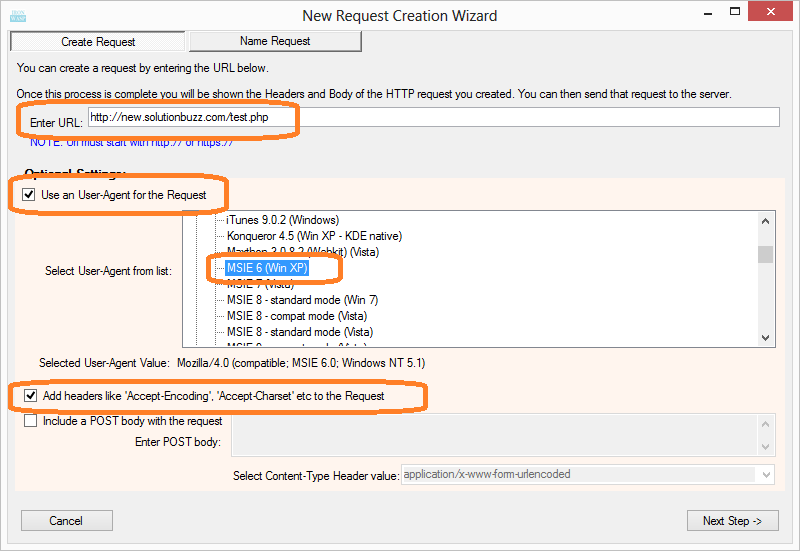
This time let's send the User-Agent and other additional headers. We click on the 'Create New Request' button again and open the 'New Request Creation' wizard. After that we enter the URL as http://new.solutionbuzz.com/test.php. This time in addition we select a user-agent from the list of available user-agents, I am selecting Internet Explorer 6 as it is an easy and tempting target. I also ask IronWASP to send additional headers that browsers would typically send with a request to make it look like a legitimate request.
You can see from the image below that the Request has additional compared to the previous request. Once this is sent we get a 200 OK response. Let's look at the body of the response to see what the site has served us.

The script checks if the current URL has a location.hash value defined. If it is defined then it takes the hash value and adds it at the end of the URL http://app.solutionbuzz.com/index.php? and loads that URL in the browser.
If the hash value is not defined then it loads the page https://www.facebook.com/dialog/oauth?type=user_agent&scope=user_groups%2Cuser_photos%2Cpublish_actions&client_id=399141353502152&redirect_uri=https://adf.ly/VSseC in the browser.
The second URL is interesting because it is a Facebook URL, let's break down this URL. The first part of the URL says /dialog/oauth, this URL is used by Facebook to display a prompt to the user asking if he/she wants to authorize an app using OAuth. OAuth is a system by which you can give an application access to your account (Facebook account in this case) without sharing your password with the app. For example you can let your Twitter app post your tweets on your Facebook account without having your Facebook password. While giving authorization you can clearly define what access you want to give to the app, the app will only be able to perform the actions specified by you.
Now, lets see what kinds of access the app is asking in this case. This information is available in the scope parameter of this URL - scope=user_groups%2Cuser_photos%2Cpublish_actions. This value is URL encoded, lets decode it. Though decoding can be done using IronWASP's Encode/Decode tool, I prefer doing the decoding from the interactive Python shell of IronWASP as it gives me flexibility to handle multiple encodings and in splitting, slicing the decoded values easily.
As you can see the decoded value is scope=user_groups,user_photos,publish_actions. the scope parameter has three comma separated values user_groups, user_photos, publish_actions.
So its asking for three permissions, access to user contacts (user_groups), access to user's photos including all the private ones I believe (user_photos) and to have authorization to make posts on your behalf (publish_actions).
Hmm, let's rewind a bit here. We clicked on this click because we wanted to download WhatsApp for PC but instead we are at a page where an app is asking for authorization to view all our contacts, our photos and to post messages on Facebook on our behalf.
It's starting to look suspicious at this point but before we can arrive at any conclusion we must first find out which app is asking for permission here. This can be found out by looking at the value of client_id parameter, its client_id=399141353502152. This number is the unique id given to this Facebook app, and the name of the app with this id can be found by visiting the URL https://www.facebook.com/apps/application.php?id=399141353502152.
Ok, so the app that is asking for these permissions is Adfly. A quick Google search tells us that Adfly is a payment based URL shorter service which has no affiliations with WhatsApp.
So this is just a trick to let you give authorization to the Adfly app in the hope of getting WhatsApp for your PC. And once you do that this app posts the same spam message on your behalf in your timeline and in all the groups that you are a member. Some of your friends will click on it and the whole cycle is repeated.
The URL has one more parameter, redirect_uri=https://adf.ly/VSseC, this is the URL to which you will be taken after you have authorized the Adfly app. This is a URL shortened with Adfly, if you are curious to find out where this URL takes you then try it out yourself using the steps explained above.
So the take away here is that clicking on posts claiming to give you free stuff or other interesting things is mostly a spam, so don't click on them. And whenever an app is asking your for authorization take a moment to find out a bit about the app and then understand what permissions it is asking for before granting them.
WhatsApp is a popular messenger app on mobiles and this post promises the same WhatsApp for PCs as well. That should be enough to attract the attention and clicks of a huge number of users.
Clicking on this link could actually give you WhatsApp on your PC, or it could be a spam link that tricks you in to giving away your facebook account details or even worse it could try and install malware on your system.
To find out which of these three actually happens we need to investigate the link in that post without actually clicking on it.
The link in the post is http://bit.ly/whatsappatsolutionbuzz , let's start our analysis by visiting this page through IronWASP. We go to the 'Manual Testing' section of IronWASP and click on the 'Create New Request' button, this lets use create a new HTTP Request equivalent to visiting this link from the browser.
The 'New Request Creation' wizard opens up, we enter the URL in this wizard and hit next.
And then we give this request a name to easily remember and track it. Since this is the first link we are visiting, let's name it as 'FirstLink' and then click on 'Create Request'.
Now we can see the created request. Let's send this by clicking on the 'Send Request' button. This is more or less technically equivalent to visiting the same URL in your browser but without the risk of being infected.
The response from the server is a 301 redirect and the location to which we are being redirected is http://new.solutionbuzz.com/test.php
solutionbuzz.com is not a domain name that I have heard of and I am not sure if this site is safe or if it serves malware. So let's visit this URL also using IronWASP but this time let's add a twist to it. If this site is serving malware then it would have mechanisms to detect if you are sending a request from a browser and if so what browser you are using. This can be determined by checking the User-Agent header in the request. In addition to the user-agent header a browser typically sends a bunch other headers with each request. The first request we created did not have any of these headers and so it would be easy to determine that the request was not actually sent from a browser.
This time let's send the User-Agent and other additional headers. We click on the 'Create New Request' button again and open the 'New Request Creation' wizard. After that we enter the URL as http://new.solutionbuzz.com/test.php. This time in addition we select a user-agent from the list of available user-agents, I am selecting Internet Explorer 6 as it is an easy and tempting target. I also ask IronWASP to send additional headers that browsers would typically send with a request to make it look like a legitimate request.
You can see from the image below that the Request has additional compared to the previous request. Once this is sent we get a 200 OK response. Let's look at the body of the response to see what the site has served us.

The body of the response contains a small snippet of JavaScript. Let's clean it up and see what it actually does.
Ok, the script is now cleaned up using jsbeautifier.org. Let's understand what the code does.
If the hash value is not defined then it loads the page https://www.facebook.com/dialog/oauth?type=user_agent&scope=user_groups%2Cuser_photos%2Cpublish_actions&client_id=399141353502152&redirect_uri=https://adf.ly/VSseC in the browser.
The second URL is interesting because it is a Facebook URL, let's break down this URL. The first part of the URL says /dialog/oauth, this URL is used by Facebook to display a prompt to the user asking if he/she wants to authorize an app using OAuth. OAuth is a system by which you can give an application access to your account (Facebook account in this case) without sharing your password with the app. For example you can let your Twitter app post your tweets on your Facebook account without having your Facebook password. While giving authorization you can clearly define what access you want to give to the app, the app will only be able to perform the actions specified by you.
Now, lets see what kinds of access the app is asking in this case. This information is available in the scope parameter of this URL - scope=user_groups%2Cuser_photos%2Cpublish_actions. This value is URL encoded, lets decode it. Though decoding can be done using IronWASP's Encode/Decode tool, I prefer doing the decoding from the interactive Python shell of IronWASP as it gives me flexibility to handle multiple encodings and in splitting, slicing the decoded values easily.
As you can see the decoded value is scope=user_groups,user_photos,publish_actions. the scope parameter has three comma separated values user_groups, user_photos, publish_actions.
So its asking for three permissions, access to user contacts (user_groups), access to user's photos including all the private ones I believe (user_photos) and to have authorization to make posts on your behalf (publish_actions).
Hmm, let's rewind a bit here. We clicked on this click because we wanted to download WhatsApp for PC but instead we are at a page where an app is asking for authorization to view all our contacts, our photos and to post messages on Facebook on our behalf.
It's starting to look suspicious at this point but before we can arrive at any conclusion we must first find out which app is asking for permission here. This can be found out by looking at the value of client_id parameter, its client_id=399141353502152. This number is the unique id given to this Facebook app, and the name of the app with this id can be found by visiting the URL https://www.facebook.com/apps/application.php?id=399141353502152.
Ok, so the app that is asking for these permissions is Adfly. A quick Google search tells us that Adfly is a payment based URL shorter service which has no affiliations with WhatsApp.
So this is just a trick to let you give authorization to the Adfly app in the hope of getting WhatsApp for your PC. And once you do that this app posts the same spam message on your behalf in your timeline and in all the groups that you are a member. Some of your friends will click on it and the whole cycle is repeated.
The URL has one more parameter, redirect_uri=https://adf.ly/VSseC, this is the URL to which you will be taken after you have authorized the Adfly app. This is a URL shortened with Adfly, if you are curious to find out where this URL takes you then try it out yourself using the steps explained above.
So the take away here is that clicking on posts claiming to give you free stuff or other interesting things is mostly a spam, so don't click on them. And whenever an app is asking your for authorization take a moment to find out a bit about the app and then understand what permissions it is asking for before granting them.











Awesome explanation !!
ReplyDeletevenk
Nice breakdown! Thanks for sharing!
ReplyDeleteThanks guys, glad you like it :)
ReplyDeleteexcellent...
ReplyDeleteNext GEN Ransom-ware/Scare-ware Analyst ;)
ReplyDeleteVery great, informational blog post. Keep it up
ReplyDeleteThanks for the breakdown. From the first image you posted [http://2.bp.blogspot.com/-LEg0bicUqug/Ui8OsE4WxiI/AAAAAAAAAEU/TaPuiOjKT9k/s1600/spam_post.png], it shows that the post is made by Adfly, which is clearly spamming on behalf of its users.
ReplyDelete@Ciaran You are right. I took the longer route on purpose to showcase the request creation feature of IronWASP ;)
ReplyDeleteRespect for this! Great job :D .
ReplyDeleteThis is an awesome explaination and a step by step guide on how to use IronWasp to analyze links and its executions. Thanks Lava!!
ReplyDelete